(Created page with 'Secure Tunnels or "stunnels" as they are commonly referred to are an amazing feature of SSH. They allow you to perform port redirection through an encrypted tunnel between hosts....') |
(No difference)
|
Latest revision as of 19:17, 4 July 2012
Secure Tunnels or "stunnels" as they are commonly referred to are an amazing feature of SSH. They allow you to perform port redirection through an encrypted tunnel between hosts. Think of it as an application specific VPN.
Possible Uses:
- Remote Desktop to a PC behind a firewall.
- Bypass my employers Proxy server, by forcing all my HTTP traffic through my home firewall (and its all encrypted).
Linux / BSD
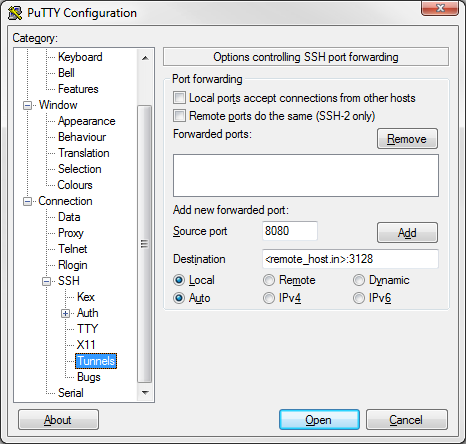
This example can be used to connect to a remote proxy server.
ssh -f -N -L 8080:<remote_host.in>:3128 <user@remote_host.out>
Explaination:
8080 = Local listening port <remote_host.in> = The IP or Hostname of the SSH server you will be connecting to (in most cases this will be the Inside/Private Interface). 3128 = The remote hosts listening port (in this case its squid's default listening port). user@remote_host.out = The IP or Hostname of the SSH server you will be connecting to (in most cases this will be the Outside/Public Interface).
Windows
We will use the same example as above, only for windows we will use Putty to establish the connection.
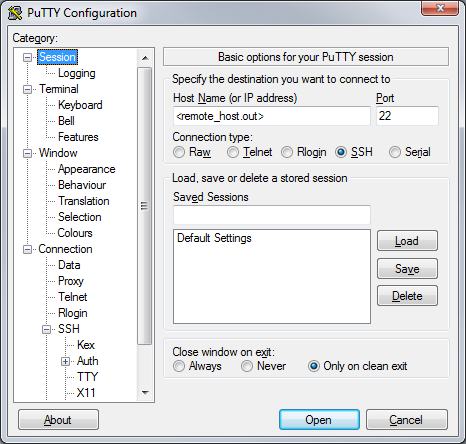
Connecting to the Remote SSH Server
RDP behind Firewall
Here is an example of how to use a stunnel to connect to a remote PC behind a firewall (assuming the firewall allows SSH connections).
Connecting to the Remote SSH Server

Launch an RDP session
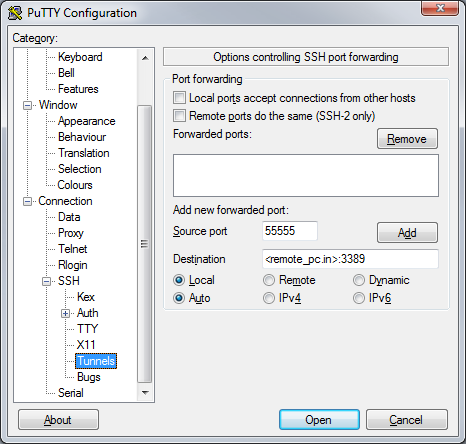
This may seem counter intuitive for an RDP connection, but the stunnel's local listening port is waiting for connections on 127.0.0.1 (aka localhost) at port 55555.
All traffic (in this case RDP) sent to this port will be encrypted and passed through the tunnel and out the other side to <remote_pc.in>:3389 (where 3389 = default RDP port).
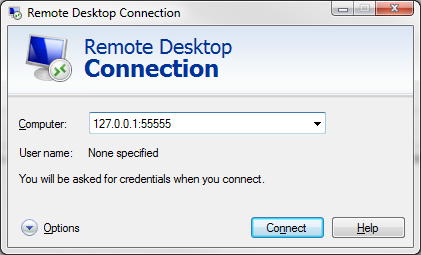
<remote_pc.in> = The IP or Hostname of the PC you want to RDP into behind the firewall.
The Linux / BSD command line equivalent is:
ssh -f -N -L 55555:<remote_pc.in>:3389 <user@remote_host.out>
SSH Command Reference
-f Run in the background. -N Do NOT execute a remote command. -L Local binding address.